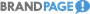Amid the panicked response this week to the news of significant, though not-yet-exploited, vulnerabilities in the vast bulk of the world's microprocessors, it went almost unnoticed that most browser makers responded by updating their wares in the hope of fending off possible web-based attacks.
The Google-driven revelations - it was members of the search firm's Project Zero security team who identified the multiple flaws in processors designed by Intel, AMD and ARM - were to go public next week, on Jan. 9, this month's Patch Tuesday. At that time, a coordinated effort by multiple vendors, from OS developers to silicon makers, was to debut with patches to protect, as best could be done without replacing the CPU itself, systems against flaws grouped under the umbrella terms of Meltdown and Spectre. That plan went out the window when leaks started to circulate earlier this week.
While the most important fixes distributed so far came from chip makers and operating system vendors, browser developers also updated their applications. That's because Spectre could be leveraged by criminals using JavaScript attack code posted on hacker-run or compromised sites.
According to a group of independent and academic researchers, "Spectre attacks can also be used to violate browser sandboxing, by mounting them via portable JavaScript code." The researchers also wrote a proof-of-concept that demonstrated how an attacker could use JavaScript to read the address space of a Chrome process - in other words, an open tab - to harvest, say, site credentials that had just been entered.
Some of the biggest browser names have already created and distributed updates designed to protect the applications - and the data on the device - from potential Spectre attacks, although as of now, patches for Apple's Safari remain AWOL.
Google Chrome
Google updated Chrome for Windows, macOS and Linux to version 63 about a month ago, and in that version debuted new security technology, dubbed "Site Isolation." This week, Google urged customers to enable the feature - it's off by default in Chrome 63 - to better defend against Spectre attacks.
 IDG
IDG
Site isolation in Chrome 63 can be switched on by enabling a flag found at chrome://flags/#enable-site-per-process
Site isolation was a step up from the already-in-Chrome by-tab process assignments, and is designed to block remote code that does execute within Chrome's sandbox from manipulating the content of other tabs. The implication was that isolation would prevent attackers from exploiting Spectre to grab in-memory data held within the addressable memory of a non-active tab.
Site isolation can be switched by enabling a flag found at chrome://flags/#enable-site-per-process; enterprise IT managers can enable and manage the option via Windows' Group Policy. More information about the latter can be found on this Chrome support page.
Google will add more anti-Spectre defenses in Chrome 64, slated to ship the week of Jan. 21-27. Among those additional mitigations, Google highlighted modifications to Chrome's JavaScript engine, V8. Other, unnamed, steps will be taken with later Chrome upgrades, Google pledged.
Starting Friday, Google also applied the same techniques as other browser makers, including Microsoft and Mozilla, to Chrome, saying that they are "a temporary measure until other mitigations are in place." On Jan. 5, Chrome disabled the SharedArrayBuffer JavaScript object and changed the behavior of the performance.now API (application programming interface) to reduce the efficacy of Spectre attacks.
Internet Explorer and Edge
Microsoft issued updates for Internet Explorer (IE) and Edge for Windows 10, as well as IE patches for Windows 7 and Windows 8.1 this week. Those updates can be downloaded in the form of the usual Security Monthly Quality Rollup for Windows 7/8.1 or the Security Only Quality Update for the same versions.
Note: The Security Only Quality Update can be retrieved using Windows Server Update Services (WSUS) or manually from the Microsoft Update Catalog.
Microsoft took the same steps as other browser makers - the effort was clearly coordinated - including Chrome. "Initially, we are removing support for SharedArrayBuffer from Microsoft Edge (originally introduced in the Windows 10 Fall Creators Update), and reducing the resolution of performance.now in Microsoft Edge and Internet Explorer," John Hazen, a principal lead program manager with the Edge team, wrote in a post to a company blog.
"These two changes substantially increase the difficulty of successfully inferring the content of the CPU cache from a browser process," Hazen added.
Mozilla's Firefox
Mozilla updated its browser Thursday to version 57.0.4 with the same two mitigations as other browser developers.
"Since this new class of attacks involves measuring precise time intervals, as a partial, short-term, mitigation we are disabling or reducing the precision of several time sources in Firefox," said Luke Wagner, a Mozilla software engineer, in a blog post Tuesday. "This includes both explicit sources, like performance.now, and implicit sources that allow building high-resolution timers, viz., SharedArrayBuffer."
Mozilla disabled the latter in Firefox, and reduced the resolution - the smallest discrete bit, in other words - of the performance.now API to 20 microseconds. (Microsoft did the same with IE and Edge when it reduced the resolution of the API from 5 microseconds to 20 microseconds.)
The Firefox ESR (Extended Support Release) branch won't be updated until Jan. 23 to include the reduced resolution of performance.now, Mozilla said. Firefox ESR is aimed at organizations that prefer a version that goes unchanged, other than security updates, for a year at a time.
Apple's Safari
While Apple asserted that December 2017 updates to macOS and iOS introduced defensive measures to help defend against Meltdown, the Spectre vulnerabilities have not been addressed with Safari updates as of Saturday, Jan. 6.
"Apple will release an update for Safari on macOS and iOS in the coming days to mitigate these exploit techniques," Apple said in a support document published Friday.
Apple did not spell out the mitigations planned for its web browser, but they almost certainly will include disabling of SharedArrayBuffer and a reduced resolution for the performance.now API, the two steps taken by rival browsers.